My previous post detailed the process to install AWS Landing Zone Accelerator (LZA) within an existing Control Tower environment. While the process wasn’t trivial or all that well documented, it did result in a successfully deployed LZA. What are the benefits that LZA provides out of the box beyond a basic Control Tower deployment? Using the LZA standard config, I will highlight the major features that differentiate LZA from Control Tower.
Logging Account
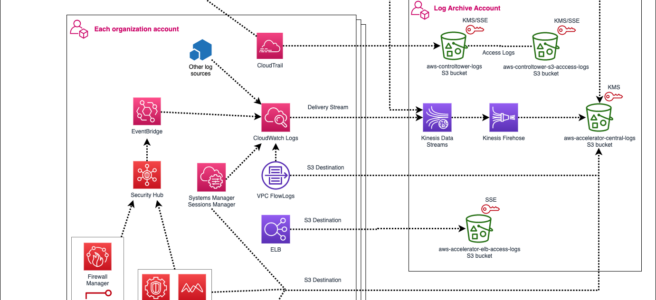
Centralized logging is one of the key components for any AWS landing zone. Control Tower deploys a MVP (minimum viable product) logging solution to get customers started with the concept of centralized logging. Control Tower provides a logging account and an organizational level trail that logs all events for the management account and all member accounts in the organization. It also provides the governance required to lock down organizational logging.
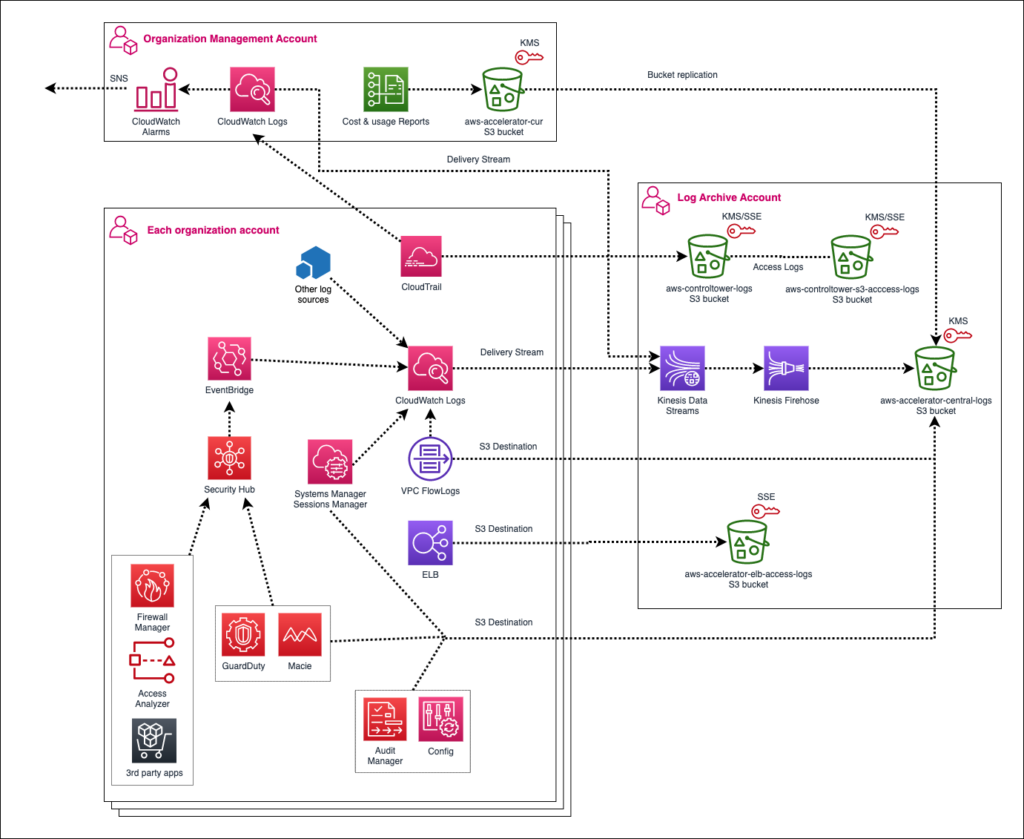
Control Tower utilizes AWS Cloud Trail, AWS Config and CloudWatch to build a logging solution that gets customers off the ground. LZA expands upon the basics of centralized logging in AWS by using a more dynamic, event driven architecture to help customers tailor their logging infrastructure to meet specific compliance requirements and performance needs.
AWS LZA uses EventBridge to monitor for new CloudWatch log groups within the organization. Once that event is triggered, Lambda is used to update groups with a retention period, AWS KMS key and subscription filter. A delivery stream is configured with Kinesis Data Stream and Firehose to transform the logs and replicate them to three LZA specific S3 buckets within the logging account. The amount of automation built into this logging solution far outweighs the basic CloudTrail-centric view provided by Control Tower. For customers who have plans for more robust and flexible AWS native logging capabilities, LZA better hits that mark.
Audit Account
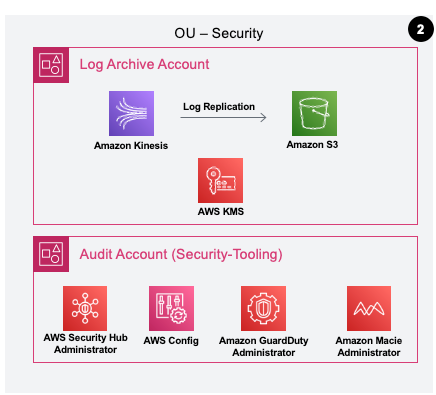
LZA largely repurposes the Audit account to be the “Security Tooling” account. This account gets assigned as the organization delegated administrator for Security Hub, GuardDuty, Macie and AWS IAM Access Analyzer. I don’t believe that it uses Audit Manager by default, but the intent is to create one location based on AWS Prescriptive Guidance to generally be used for security tooling.
This change makes logistical sense to me, as the Audit account in Control Tower seemed to bring little value as-is beyond some of the IAM roles that can be fairly easily reconstructed. This LZA account could still be used for Audit Manager to aggregate organizational wide reporting, along with what is provided by the AWS native security tooling. The name of this account is maybe a bit perplexing, but as Control Tower eventually changed the Core OU name to Security OU, maybe there will be future updates that address naming conventions.
Management Account
The Management Account is where the Control Tower Dashboard can be accessed. This account is usually available to a very small subset of AWS users, typically from an organization’s security or IT department. The Control Tower Dashboard isn’t typically a heavy lift from an administrative perspective, but would be one of the few reasons to occasionally access the Management Account.
The main purpose of the Management is to be the one stop shop for the LZA configuration itself. The two pipelines that control LZA operate from here, so updates to LZA would be performed in this account. Similar to Control Tower, the Management account still controls new account creation and drift detection within the org. LZA also brings some added Cost and Usage reports that get stored in the Master account. There are also a number of KMS keys that originate from the Management account by LZA to encrypt some of the underlying components.
Network Account
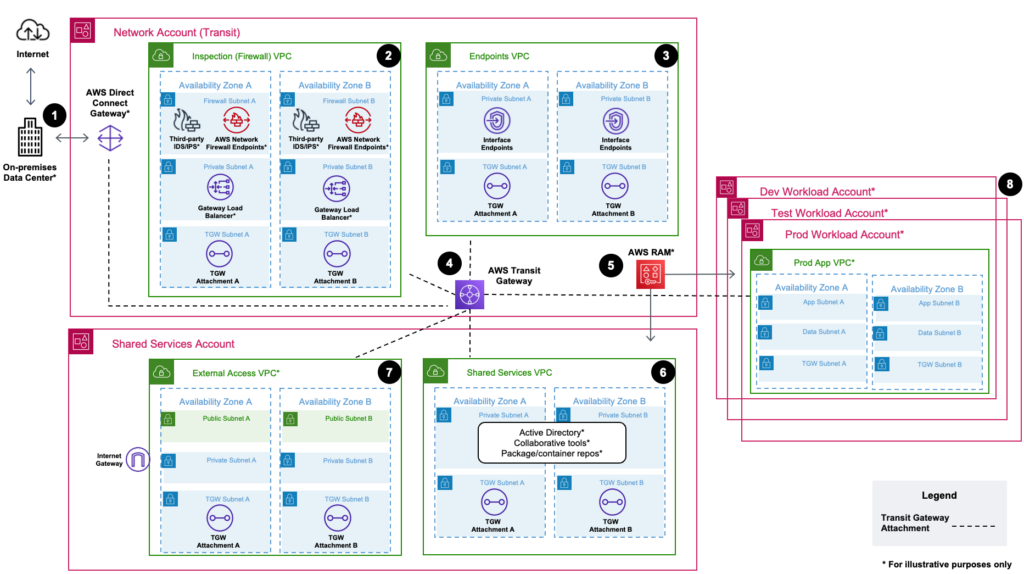
The inclusion of centralized networking is another addition that LZA brings to the table. This is one area where Control Tower typically required additional customization out of the box for many customers. It is easy enough to add a Network account after a Control Tower build, but you had to start from square one unless you already had an approved network blueprint ready and available for deployment. Most customers running Control Tower the first time would reasonably not have an AWS network architecture developed.
While LZA doesn’t magically deploy an entire plug and play network stack for you, it starts by creating the plumbing with a centralized TGW and attachments into Shared Services and other workload accounts. It also creates the skeletons for a couple of VPCs to help separate main types of network traffic. An Endpoint VPC is available to begin scaling out any endpoints that may be required by workload accounts. An Inspection VPC is also created for customers to deploy either AWS Network Firewall or third party security appliances for ingress/egress network inspection. This is a common ask for most customers, and LZA does a good job of setting the stage whereas Control Tower leaves a completely blank canvas.
Cost
LZA certainly provides enhanced scalability, automation and customization. Like most things cloud, that typically means increased consumption and increased cost. Take these numbers with a grain of salt, because my demo environment doesn’t run a bunch of AWS services at scale and may not be the best comparison against say, a large enterprise company that could put all these services through the ringer at a level that I couldn’t even imagine creating a billing alert for. In my case though, I did notice very generally these increases in landing zone specific costs after installing LZA over-top of Control Tower:
- Logging Account increased from about $5 per month to roughly $30 per month
- Audit Account didn’t see any drastic change
- Security Account increased from < $5 per month to about $50 per month (morphed into LZA Shared Services)
- Network Account increased from < $5 per month to about $170 per month
- Management Account increased between $50 – $100 per month
The added AWS consumption required to run LZA certainly comes with additional cost. That cost is negligible when compared with the benefit that LZA brings in creating more robust and customized landing zone options for AWS customers.